The other day, I was shadowing a colleague of me who was doing a red team. The client was running McAfee AV. While the reputation of that AV isn’t the best, it got a bit in the way for a few minutes.
After doing a lateral movement, my colleague was doing a procdump of the LSASS of that machine to gather more credentials to move further up the ladder of privileges he gained already.
The Dump file was created but it straight away disappeared/deleted. He got suspicious about the AV being responsible for it, and simply circumvented it by instead of dumping the lsass process to afterwards feed it to mimikatz, he used pypykatz to directly gather the credentials from inMemory. Ok so my colleague lost maybe 10min as to build and upload a pypykatz to the machine so no big deal, but it got me interested as I never saw this behaviour.
I don’t think it’s a bad idea from McAfee to do it.
I wanted to play with this in my home lab to check it out further just out of curiosity.
I recreated the environment and yes, the AV caught my lsass Dump file
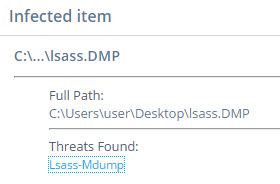
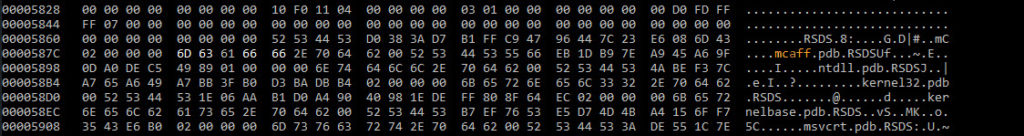
It got me into the rabbit hole of reading about the MiniDump format, but quickly couldn’t find any fields for the name of the process. Only process ID and many other fields but no name.
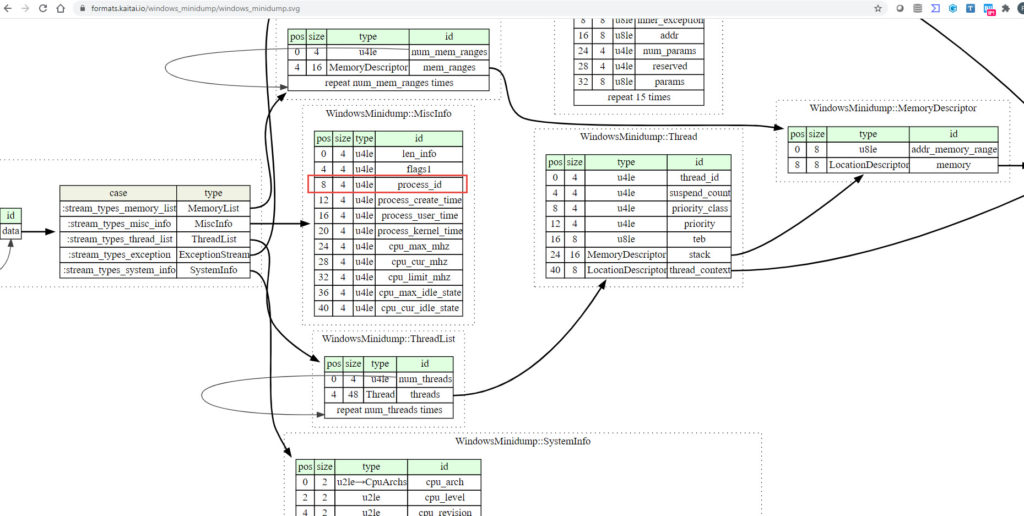
So how did McAfee detect the proc dump was from the lsass process ( as another procdump of another process didn’t trigger the signature).
A fairly string search did the job on “lsass”
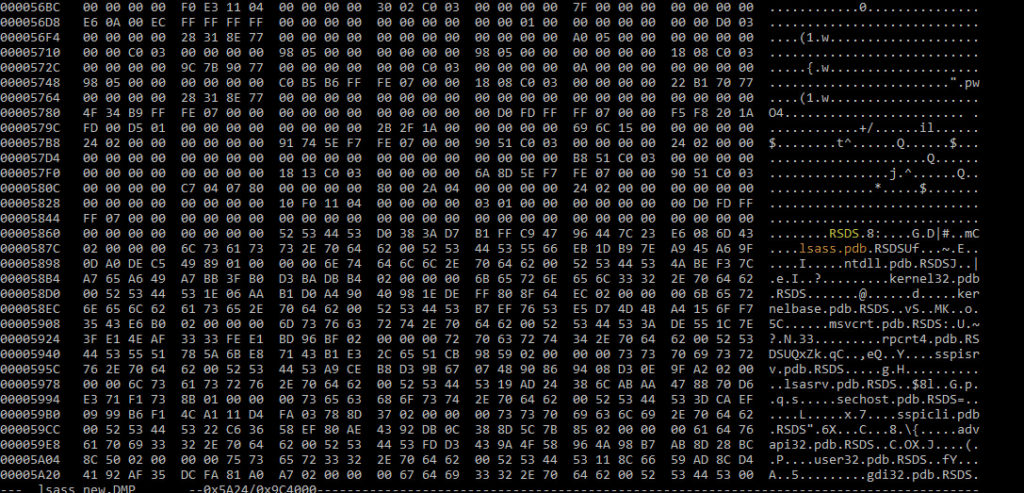
I don’t know much about forensic, but I guess when the lsass is compiled there is always a link to the possible PDB file for debugging purpose. And the first PDB reference is “lsass.pdb”
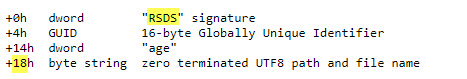
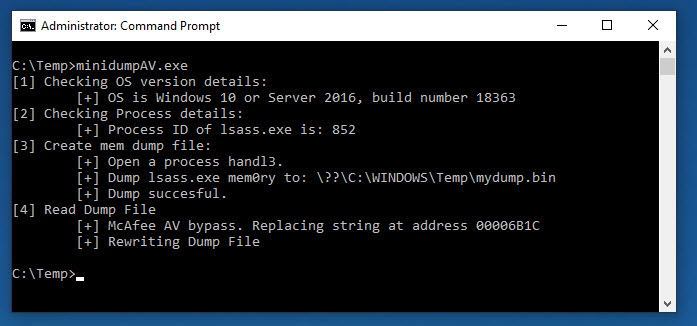
I changed that string in my dump file, et voilà, McAfee is no longer detecting it as lsass-Mdump virus and you can still feed it to Mimikatz or other.
So how many AV engines are doing this ? well only McAfee
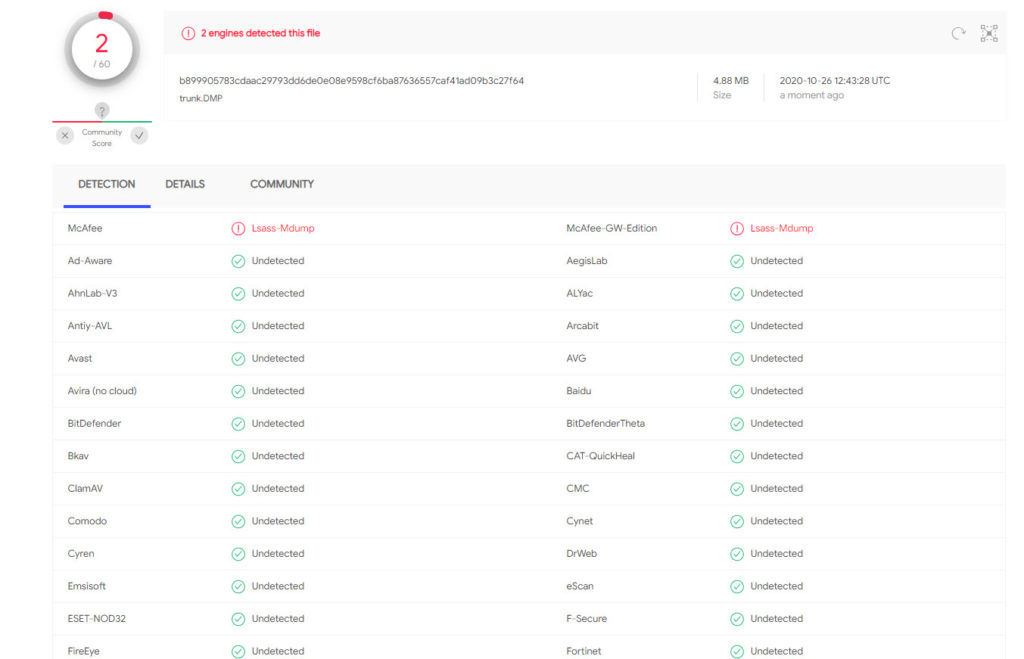
Not sure what I have achieved here but I thought it was interesting.
LSASS Dumper
I forked the Dumpert lsass dumper of Outflank and added a function to avoid been detected by McAfee AV engine.
The original project was marked as malicious by Windows Defender and a few other AV, and I might have accidentally fixed that. (including ESET AV). All string based AV detections …
Here is the source code is on my Github page : https://github.com/k4nfr3/Dumpert
Thanks to @itm4n for guidance in C
References :
MiniDump Format https://formats.kaitai.io/windows_minidump/index.html
Pypykatz : A python version of mimikatz: https://github.com/skelsec/pypykatz
PDB file information in the executable : http://www.godevtool.com/Other/pdb.htm
Outflank Dumpert original github : https://github.com/outflanknl/Dumpert
2
Recent Comments