Last few days, I’ve been playing with the WFP componant of Windows.
WFP = Windows Filtering platform
Many informations blogs are existing like the great one from Pavel who really deeped dive into it which I recommand to read
https://scorpiosoftware.net/2022/12/25/introduction-to-the-windows-filtering-platform/
I would also recommand looking/use his tool : https://github.com/zodiacon/WFPExplorer
In a nutshell for me, the little things I took out of it
- There is multiple Providers
- There is multiple Layers
- There is multiple Sub Layers
- Rules have weights
- WFP can be accessed via Kernel land OR User Land
- Rules can be temporary, or permanent (temporary = while your exe runs they exists, if your exe dies they are removed
- Most EDRs use WFP on Windows for some tasks, like device isolation
In a Nutshell, there is a few projects on this, but I’ve used on the recommendation of @nodauf the GO library https://pkg.go.dev/inet.af/wf
Not really well documentated but highly effective.
I was able to remove the Isolation feature of a 2 very well known EDRs and also stop logging all events to it’s cloud storage, this disabling quite a few detection like BIOC, User Behaviour … and in one of the EDR it feels like you are completely turning off all detection (including lsass dump)
My github project just allows this for pentesting and redteam : (at the moment it’s private repo : https://github.com/k4nfr3/WFP_EDR
A colleague of me, used the same concept on a micro-segmentation product, which is based on agents (by using WFP filtering)
If you can access the machine and succeed a priv esc, then you can completely disable the solution … Game Over
Blue Team : the only way to check on this is to enable WFP Policy changes logging events
auditpol /set /Subcategory:"Filtering Platform Policy Change"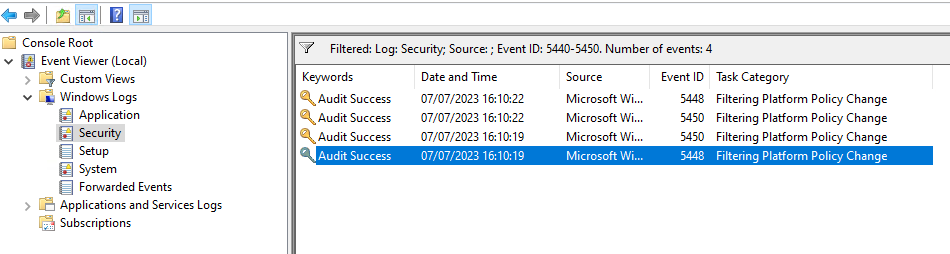
and my 2 cents here would to check the origin of the change with the ProcessID Field
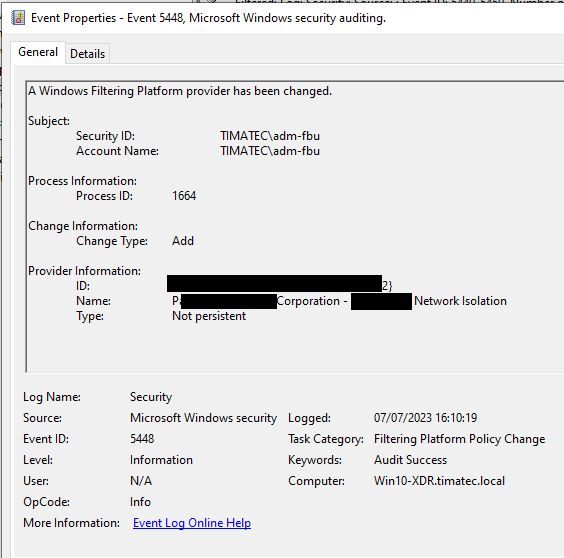
Windows Logs / Security Event IDs
5440 : The following callout was present when the Windows Filtering Platform Base Filtering Engine started.
5441 : The following filter was present when the Windows Filtering Platform Base Filtering Engine started.
5442 : The following provider was present when the Windows Filtering Platform Base Filtering Engine started.
5443 : The following provider context was present when the Windows Filtering Platform Base Filtering Engine started.
5444 : The following sub-layer was present when the Windows Filtering Platform Base Filtering Engine started.
5446 : A Windows Filtering Platform callout has been changed.
5447 : A Windows Filtering Platform filter has been changed.
5448 : A Windows Filtering Platform provider has been changed.
5449 : A Windows Filtering Platform provider context has been changed.
5450 : A Windows Filtering Platform sub-layer has been changed.

Recent Comments