This is under construction
Commands to troubleshoot your WEC/WEF Forwardings
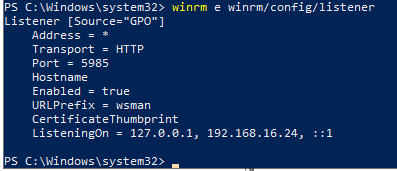
PS Code to get status of the Listener
winrm e winrm/config/listener
PS Code to get status of a Forwarding Channel
wecutil gr Security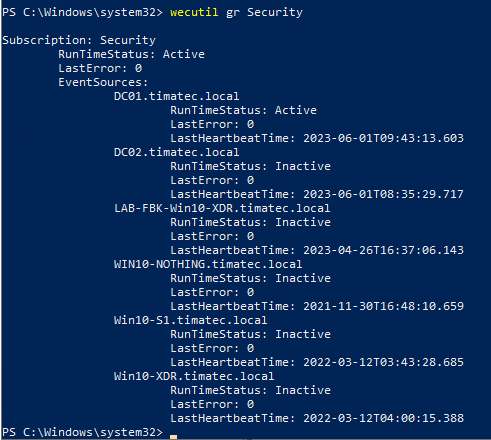
Above we see only one Active source forwarding it’s logs
PS Code to get configuration of a Forwarding Channel
wecutil gs Security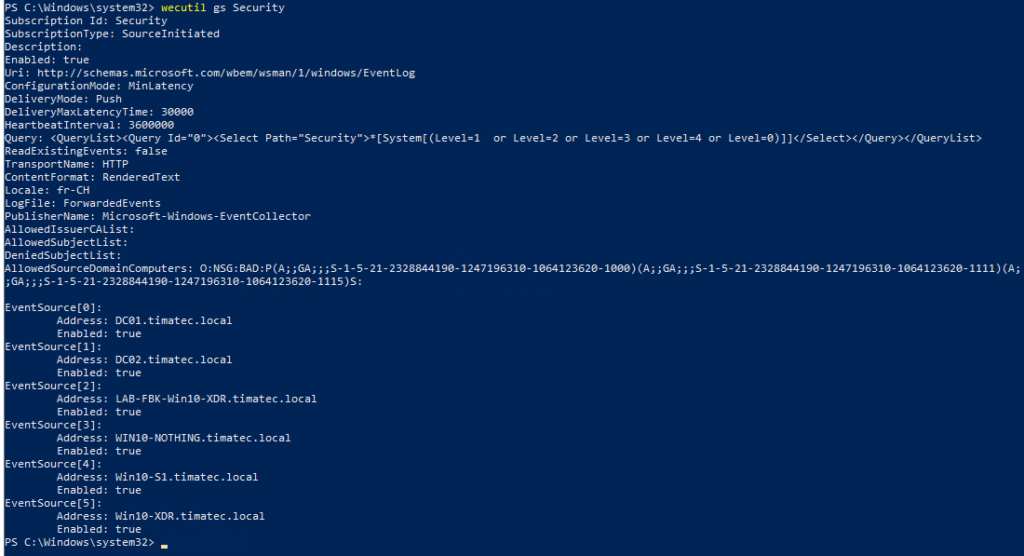
Here we see no filter on source event channel Security and the list of machines allowed to Forward by HTTP transport
Want to see the real detail of the ACL ?
ConvertFrom-SddlString "O:NSG:BAD:P(A;;GA;;;S-1-5-21-2328844190-1247196310-1064123620-1000)(A;;GA;;;S-1-5-21-2328844190-1247196310-1064123620-1111)(A;;GA;;;S-1-5-21-2328844190-1247196310-1064123620-1115)S:"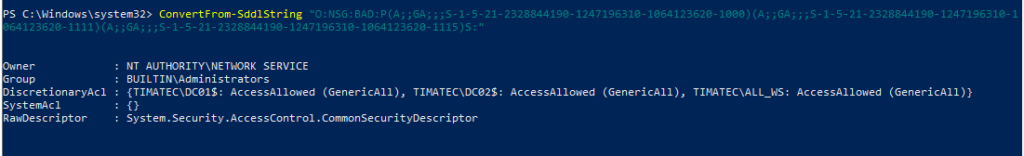
Check on your client that you get your GPO with the right subscriptions
reg query HKLM\Software\Policies\Microsoft\Windows\EventLog\EventForwarding\SubscriptionManager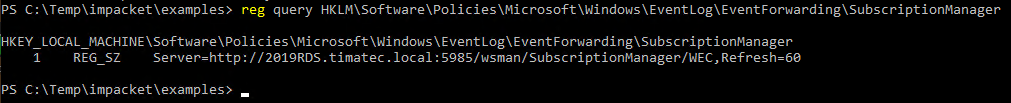
We can do a packet capture.
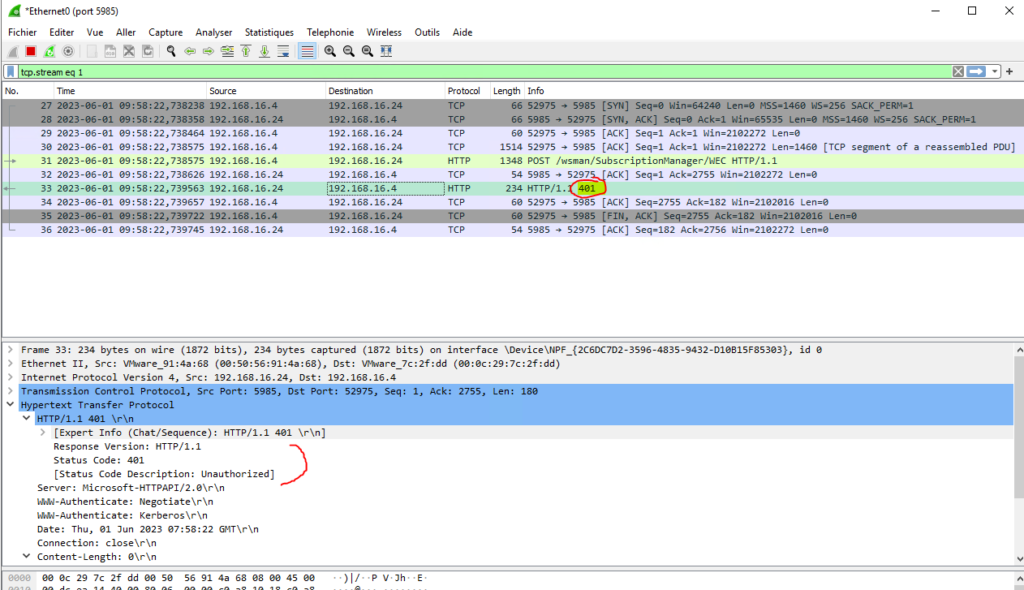
Here we can see that our WEC (192.168.16.24) is refusing the authentication from the client (192.168.16.4)
Check if the SPN has been set for the WEC Server
On the client (192.168.16.4)
setspn -F -Q */2019RDS.timatec.local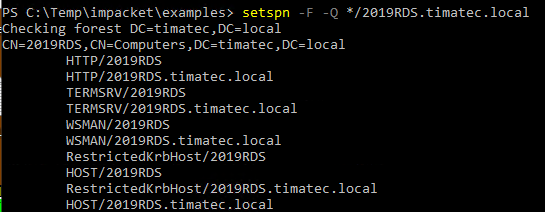
SPN are port based defined. We can see here that we are missing
Let’s add the missing SPN to solve the issue (one in FQDN and one without the domain name). 5985 Been my HTTP transport port.
setspn -S HTTP/2019RDS:5985 2019RDS
setspn -S HTTP/2019RDS.timatec.local:5985 2019RDS
setspn -F -Q */2019RDS.timatec.local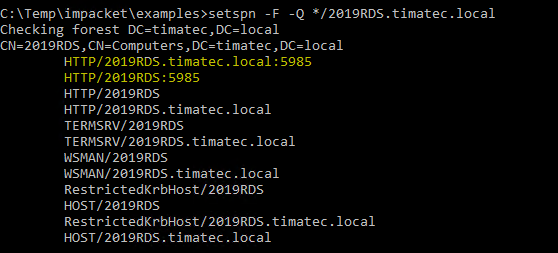
In the Wireshark on the server, it looks much better
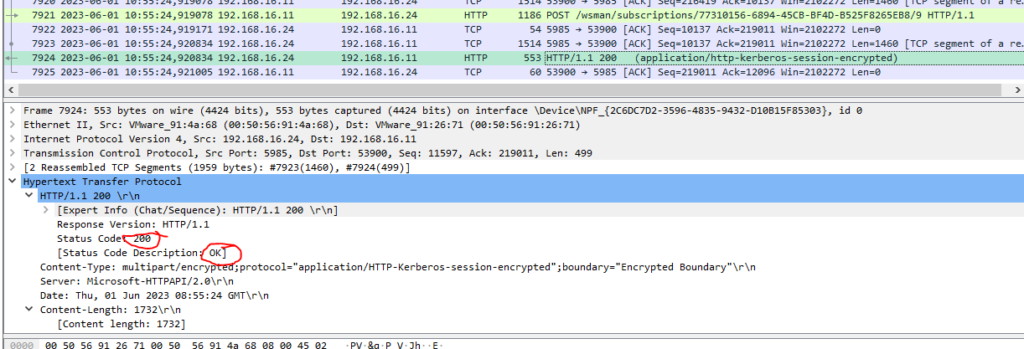
Nevertheless it looks like it’s still not working fully
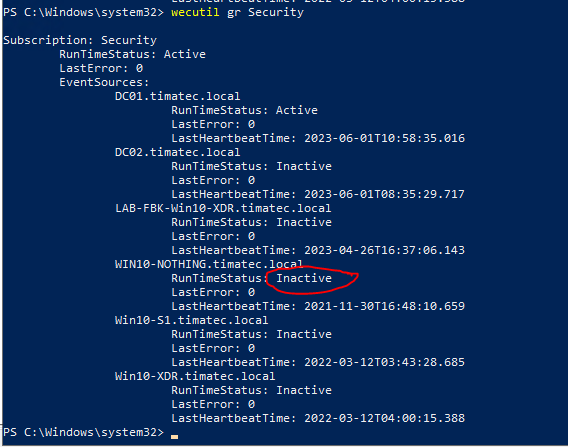
Let’s look at the WEF events on the server
MMC / Event Viewer
Applications and Service Logs / Microsoft / Windows /
I still error logs from Yesterday.
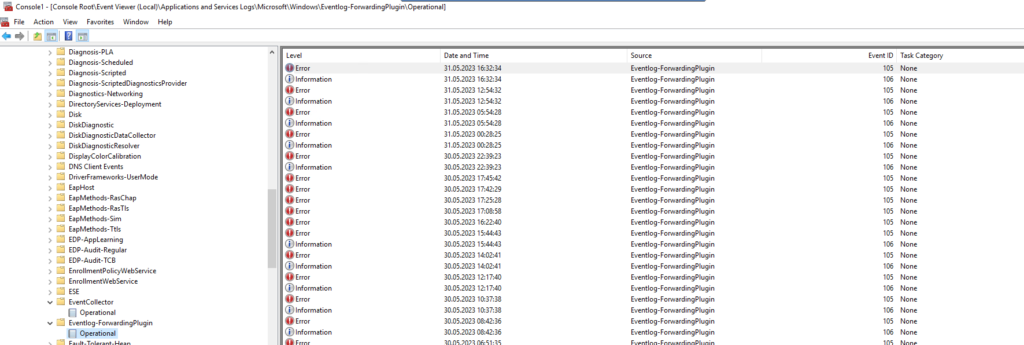
let’s restart the WEC
sc stop winrm
sc stop wecsvc
sc start wecsvc
sc start winrm
Recent Comments