This is the 3rd article in this serie. (here is part1 & part2)
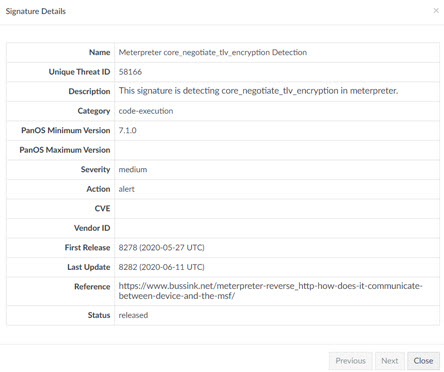
A little adon to Part 1 & 2, as part of my job is to implement Palo Alto Networks Firewalls, I took the task to work with PaloAltoNetworks for them to create a signature to detect the initial communication after the DLL is uploaded . It took a while but they finally released a signature (not sure why they only published it as alert only …pfff ). This will detect the C2C channel for Metasploit 5.x Signature for PANOS : https://threatvault.paloaltonetworks.com/?query=58166 .
So far Fortinet and Checkpoint FW still doesn’t detect it. I didn’t test on Cisco, but I have my big doubts on it.
How to detect C2C in general
There is so many varieties of Command and Control frameworks and different types, here is a few examples. What the below list example have all in common, is that they all do legitimate traffic and probably are using sanctioned application from your company network ! So to discover them. Good Luck.
- GCAT = Using Gmail as a command and control server
- Slackor = Using Slack as command and control server
- Twittor = Using Twitter as command and control server
- Dali = Using Imgur as command and control server
- Dnscat2 = Using DNS as Command and Control
- Icmpsh = Icmp command and control
- DropC2 = Dropbox command and control
- TrevorC2 = Legitimate Command and control over Http
- Sneaky-Creeper = A mixture of different social media as Command and Control (Twitter, Tumblr, Soundcloud, Salesforce, Google Spearsheets)
- SNICat = uses TLS SNI to exchange data during the HELLO phase
What they do all have in common ? They work as command and Control by definition. So the implant sends a beacon to the server and asks for a command to execute. If there is no command waiting for the client, it goes back to sleep for a period of time.
Ok, can our Firewalls detect it and we can stop it ? yes and no.
- The first line of defense is to do application layer Firewall Policy Rules. For example, Using port 80 should not be anything else than HTTP traffic. This is why I’m fan of Palo Alto Firewalls, as they are the ones who brought that in the game in 2007 ! Yes, ladies and gentlemen, you read me correctly. 13 years ago !!! Many vendors now do it more or less efficiently. Gartner branded the term “NextGen Firewalls” in 2009 ! I don’t know the real answer, but do you know how many Firewalls configured in companies facing the internet are using proper application rules ??? Probably not many enough. And what about in between segments within a company ? a lot of work is needed first on that level. As this is really time consuming. And what I like in version 9.0 of PAN-OS. On a given firewall rule it will look and list all the seen apps and propose to add
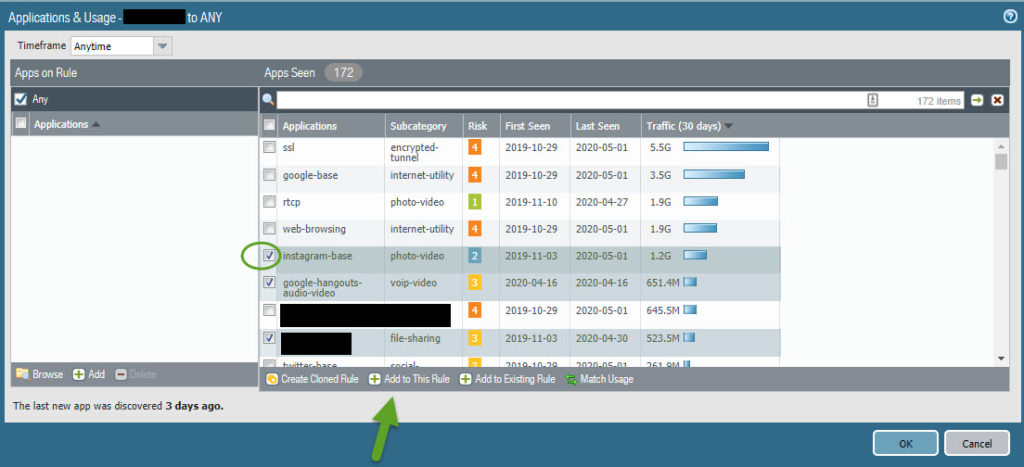
2. The second line of defense we saw in the previous article, is the SSL intercept to catch unencrypted data in a TLS connection which will then feed the payloads to the AV and Sandbox modules.
3. Third line of defense as described in the 2nd article, if there it’s normal ssl or web-browsing, is to block known malicious file type. (PE, DLL etc..)
4. Fourth line of defense, as described in the 2nd article, if the file type is unknow, we could block it. The only problem is that many web based applications use unknown file type so for most people it’s a no go.
Beacon detection is difficult. A few security appliances will detect regular beacons, or long connections. But now days, many C2C implement random period between two beacons.
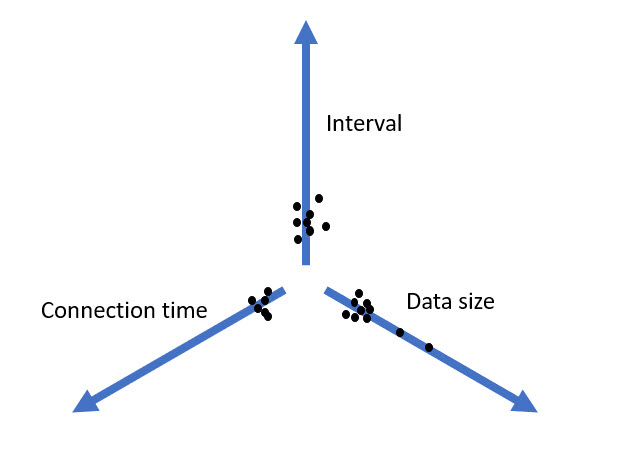
If you represent the statistics of those beacons in three axes : Interval, Connection Time and Data size.
RITA
Black Hills Information wrote a nice tool called RITA (Real Intelligence Threat Analytics) https://www.blackhillsinfosec.com/projects/rita/
The core of this tool is to analyse not the content, but stastistics on the Interval, Connection time and Data size and correlated this. It will generate a beacon score.
I installed it in my lab, and am running a Zeek span service on all incoming and outgoing traffic.
I have a dedicated VM for this (follow strictly the RITA installation guide as the program has many dependancies), on which hourly I will import the bro/zeek data into RITA
05 * * * * /usr/local/bin/rita import –rolling –numchunks 48 /opt/bro/logs/$(date –date=’-1 hour’ +\%Y-\%m-\%d)/ home > /dev/null 2>&1
As RITA is an open source project, it doesn’t come yet with an alerting mechanism etc…. to compare to their commercial product AI.Hunter. Fair enough. They have already open sourced their code, and this is fantastic. So I decided to try to automate some stuff. I’m a terrible developer and have spent several hours to get to this results (yes, I’m slow) . I have published my python3 scripts here if it helps somebody : ![]() https://github.com/k4nfr3/ritadnspysolver
https://github.com/k4nfr3/ritadnspysolver
My first script was that when seing the results I was missing the DNS name. As the data was already in the Mango database, ritadns.py will just check if the IP is in the DB.
Rita-python.py is to run rita commands but get the DNS records inside the results
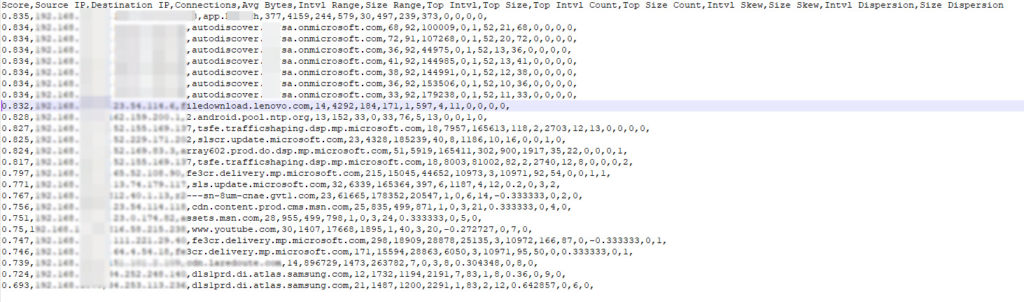
Rita-alerter.py is a script which I run from my crontab after importing the RITA results every hour, in order to trigger alerting. At the moment, I’m wrote it to send syslog alerts if it is a new alert (you can set the threshold score). The syslog alerts is then feeding into my XSOAR (aka Demisto) to automate the response ( enriching the data by getting the device name which triggered the alert / the ASN of dst IP/ Organisation / virus total / threat Crowd and so on …. ). I then received it on my Mobile Phone via a push notification alerting me in near real time (still once a hour)
While RITA mentions that there might be a few false positives, I do have quite a lot of false positives. So many softwares have a beacon mechanism for updates, content updates and so on.
Link to Black Hills Information Security webcast on RITA : https://www.youtube.com/watch?v=eETUi-AZYgc
Thanks again to the Black Hills guys who spent time thinking of it, developping it and pubishing this tool. Not sure yet, how to use it in a real world environment for the moment, due to the high number of false positives I personally experienced but it does catch all the C2C I have seen and tested with.
0
Recent Comments