SysInternals, did promised it, and they delivered.
Version 13 of Sysmon now comes with Id Event 25 which detects process hollowing and herpapining.
This off course, would mainly be used by attackers when targeting systems which have a GPO App Locking policy in place or a way to bypass some sec toolds EDR/next-gen AVs.
This event is trigguered when a detection happens between a difference of the initial image/process to be something different than the process it was launched with.
Schema needs to be updated to version 4.50
<ProcessTampering onmatch=”exclude”>
</ProcessTampering>
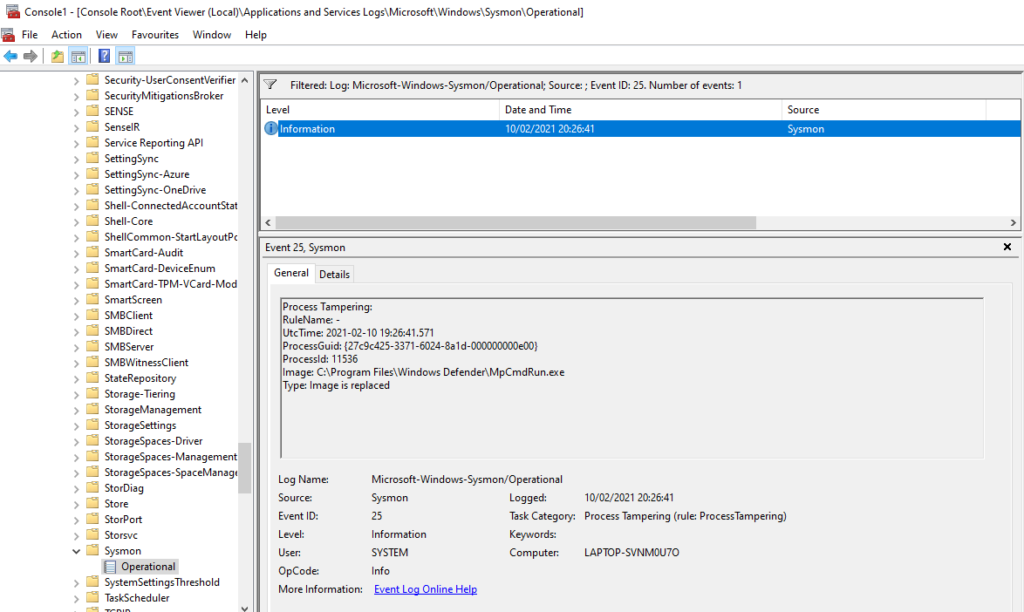
My below test print screen is of a process hollowing done on the executable MpCmdRun.exe
N.B. Only a corrolation of other events and information will be able to give the source of the process hollowing, but the important thing is that a process hollowing was detected !
The mices will live another day because there seems to be a lot of False positives with this event ID 25. After now a few weeks here is the common list of exe that generated Event ID 25 which are FP : Teams.exe, Chrome.exe, default-browser-agent.exe of Firefox, identity_helper.exe from Edge
Reference :
Olaf Artong article: https://medium.com/falconforce/sysmon-13-process-tampering-detection-820366138a6c
0
Recent Comments