Sysmon is an official SysInternals driver that let’s you log all what is happening to a Windows machine. I will not drill down here what it is capable of and how important it is to have it running on your company assets and to get them to log to a WEC (Windows Event Collector) which in turn can then log to a syslog based DB server (Splunk, Elk etc…). This is the main core information feed of a SOC.
Installing the sysmon with a simple command of
sysmon -i
but if your machine gets pwned, then the attacked could easily spot the process name
Now, you can rename the executable to something more stealthy, something that you see a lot of legit ones like RuntimeBroker.exe, svchost.exe, dllhost.exe
ok, but then if you check the service, it’s still obvious in the description
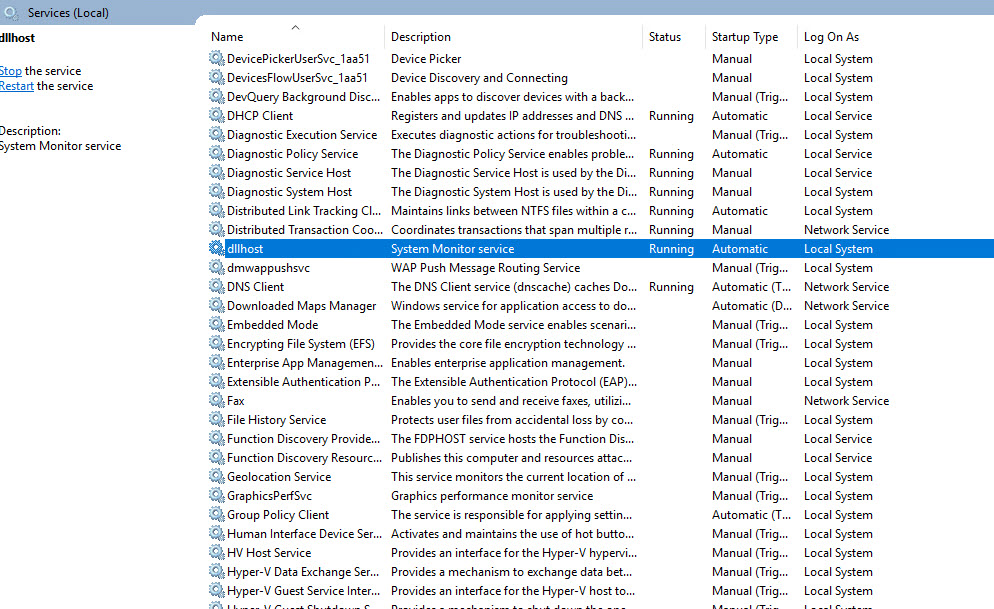
One can change the description of the service too
Get-Service -Name xxx | Set-Service -Description "new description"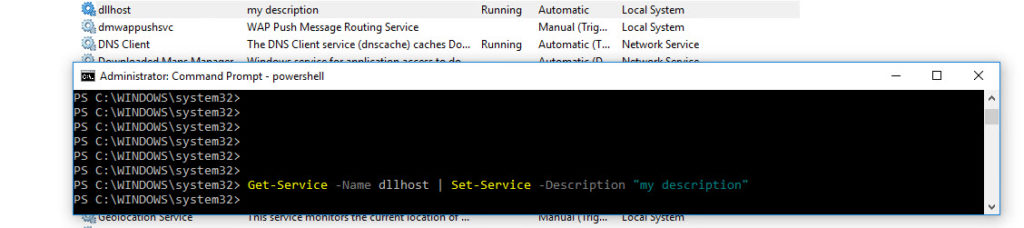
I was looking into finding the SysmonDrv in the driverquery but could’t find it.
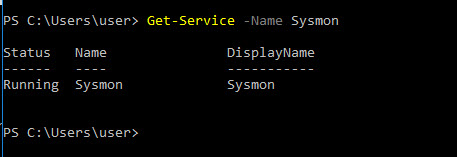
Another way to see if SYSMON is running is in powershell to check
ls HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels | Where-Object {$_.name -like “*sysmon*”}
When the service is running the key exists and Property Enabled = 1
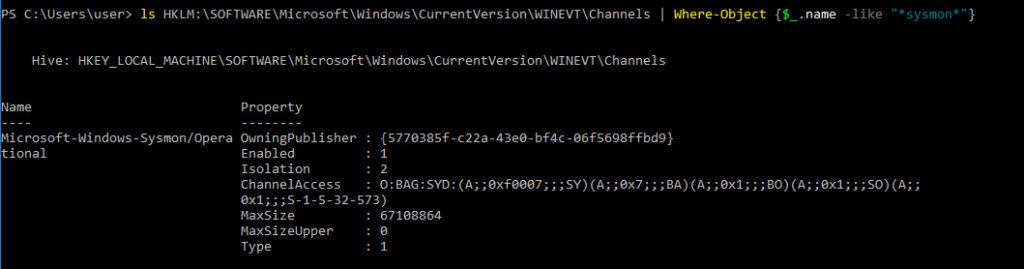
When I uninstalled sysmon, that key disapeared.
If you are Admin, you can also use the fltmc command
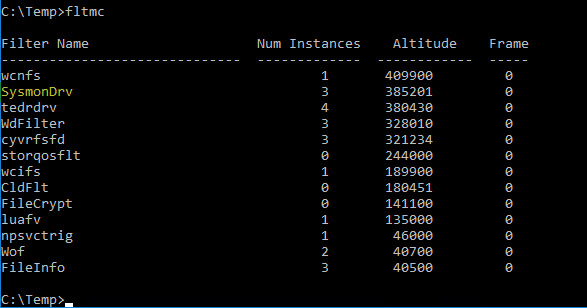
Sysmon installation process let’s you the ability to rename the driver with the -d option (8 char max): example
sysmon.exe -i -d MyDriverBut Sysmon will still be spotted by finding the Altitude of 385201 (order at boot hardcoded in Sysmon) and also if you look at the instances you still find your Sysmon name
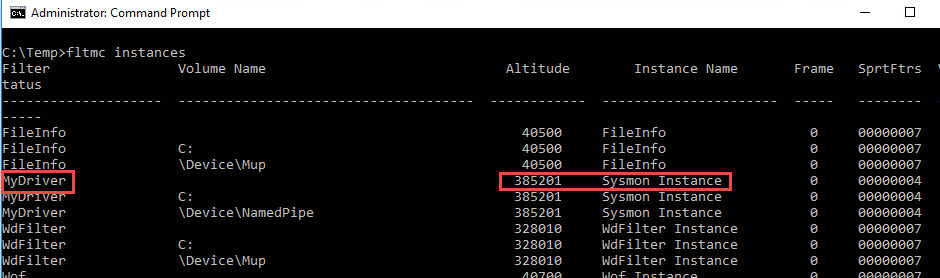
It is possible to change the altitude of the driver. But this value has to be carefully checked not to clash with another driver.
reg add "HKLM\SYSTEM\CurrentControlSet\Services\MyDriver\Instances\Sysmon Instance" /v Altitude /t REG_SZ /d 371234 /f( If you want to make sure not to clash with another driver, you get check all the allocated altitudes at the microsoft web site :
https://docs.microsoft.com/en-us/windows-hardware/drivers/ifs/allocated-altitudes
Then the last resort (to my knowledge) to detect if sysmon is running check the following registry key :
reg query HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Microsoft-Windows-Sysmon/Operational
The answer will also give you the standard GUID of Owning Publisher
Which will give you access to the system name under which sysmon is hiding under
reg query "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Publishers\{5770385f-c22a-43e0-bf4c-06f5698ffbd9}"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Publishers{5770385f-c22a-43e0-bf4c-06f5698ffbd9}
(Default) REG_SZ Microsoft-Windows-Sysmon
ResourceFileName REG_EXPAND_SZ C:\WINDOWS\onedrv.exe
MessageFileName REG_EXPAND_SZ C:\WINDOWS\onedrv.exe
Enabled REG_DWORD 0x1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Publishers{5770385f-c22a-43e0-bf4c-06f5698ffbd9}\ChannelReferences
You can after that, find the real name of the driver file with the following
reg query "HKLM\SYSTEM\CurrentControlSet\Services\onedrv\Parameters"HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Sysmon64\Parameters
DriverName REG_SZ ofltdrv
Sysmon is running in user mode. It is possible to kill it but a event ID 4 would be created. A good managed SIEM should alert on this.
You could also unload the driver ( would still log all DNS events). With command fltmc unload MyDriver (Blueteams would spot normally an event ID 255.
You could alter it’s config see this blog post : https://talesfrominfosec.blogspot.com/2017/12/killing-sysmon-silently.html
Or you can try Batsec’s proposal to disable events to be sent to sysmon :
to be runned as system.
logman stop EventLog-Microsoft-Windows-Sysmon-Operational -ets9/6/2020 – today, I stumbled on the famous Matterpreter github repository, and he wrote a little program to automate this : https://github.com/matterpreter/Shhmon lol
reference :
Sektor 7, RED TEAM Operator: Windows Evasion Course
Microsoft : https://docs.microsoft.com/en-us/windows-hardware/drivers/ifs/allocated-altitudes
4
Recent Comments