On Friday the 20th of December 2019 we realized that for a customer, the files that were analyzed by the Wildfire of PaloAltoNetworks via the TMS in Europe was using the Wildfire engine based in the US !
I raised an ticket, and with the help of our PAN SE, this issue was really quickly confirmed and mitigated in 9 days.
Here below the official Email sent to all EU TMS clients this morning the 31st of Dec 2019.

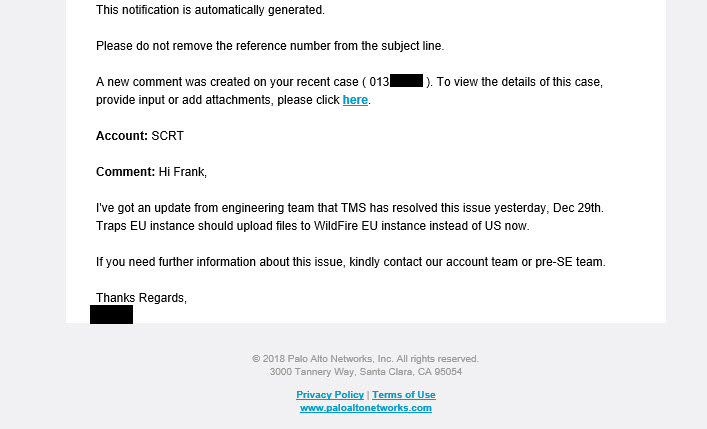
In order to prove my suspicion, I generated a new windows executable which of course had a unknown hash. I executed it on a VM which had Traps installed, so I knew it will upload the Exe file to TMS.
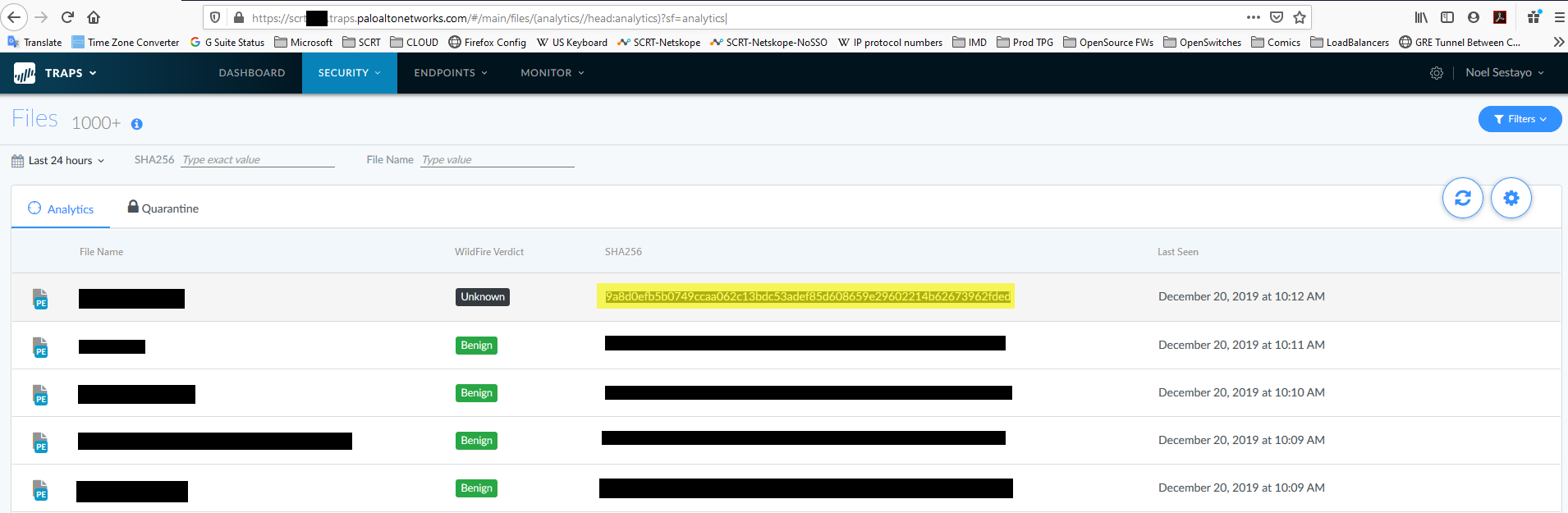
In the EU console of Wildfire, this hash didn’t return anything.
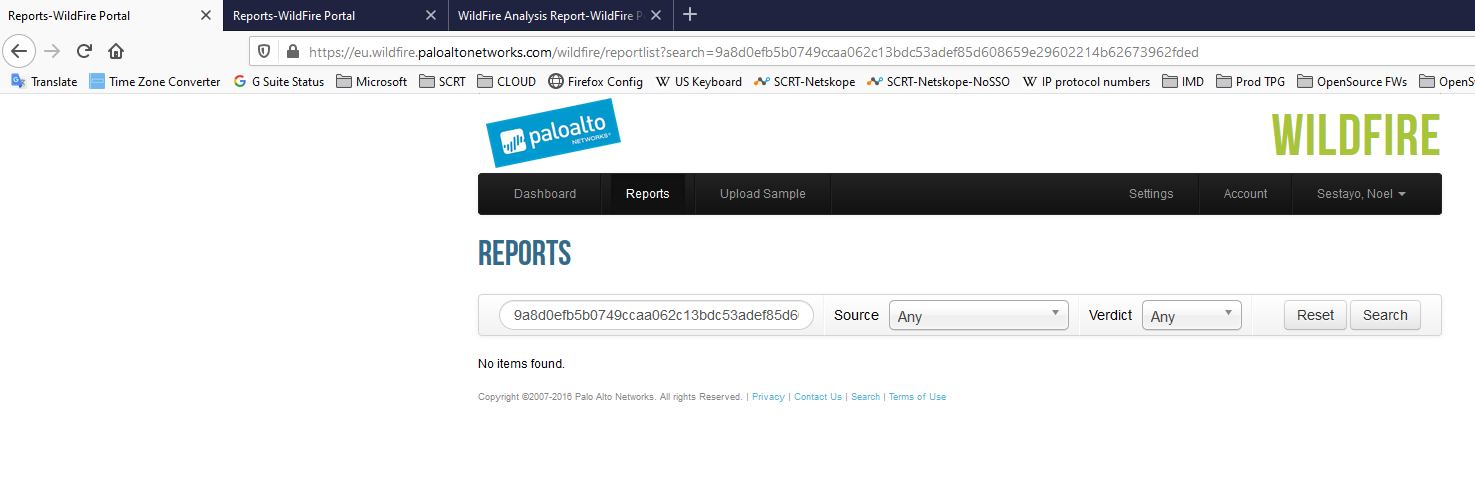
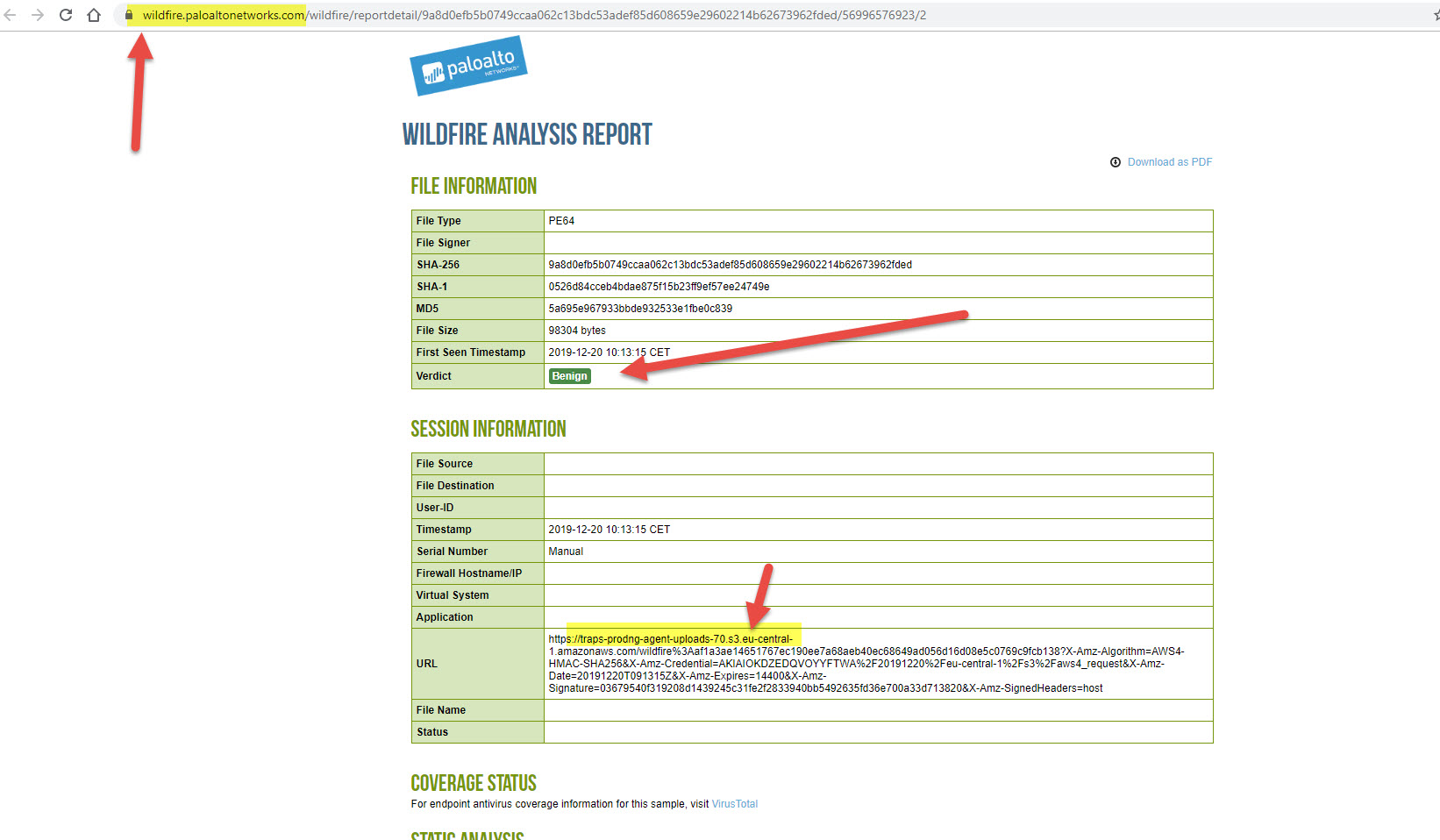
But it did in the US global one ! And you can see it cames from the EU TMS instance.
In the Age of CLOUD computing and GDPR regulations and the US having the Cyber ACT and CloudAct which could enable the US government to request access to files if located on the US Territory.
Palo alto has respected the GDPR as it is declared in the Privacy Shield framework but to our customers based in EU & Switzerland (Financial, Pharmaceutical and other branches) this issue was sensitive.
PAN in their email, stated that the data “have not been accessed by any unauthorized parties”

Recent Comments